IEN builds a Network Infrastructure for Web 3.0
What is IEN? IEN is an abbrevi…
工信部回复推进Web3.0高质量发展的政协提案
23年12月19日,工信部网站上公开回复了吴杰庄委员《关于推…
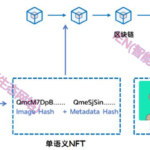
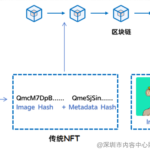
所有权富语义NFT钱包:互联网Web3.0的数据资产保险箱
互联网Web3.0作为下一代互联网,逐渐崭露头角。在Web …
富语义NFT: 互联网3.0 数据要素流通血脉
2023年10月25日,国家数据局正式揭牌,数据将成为继土地…
Semantic-Rich Ownership NFT Wallet: Data Asset Safe of the Internet Web3.0
The Internet Web3.0, as the ne…
Computing convergence is also Web3.0
Web3.0 is seen as the next gen…
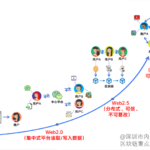
Layout strategy in the Web3.0 era
With the rapid development of …
Web 3.0底层逻辑:智能生态网络IEN-内容中心安全智能链网融合架构
导读:Web3.0 强调用户为中心,隐私数据保护,基于区块链…
Web3.0 商业模式 — 智能生态网络IEN
导读:一、Web 3.0 丞需“自底至上”的思维方式(理念,…